7th Pay Commission: सरकार जल्द केंद्रीय कर्मचारियों और पेंशनभोगियों के डीए एरियर भेजेगी। कर्मचारियों को अपने खाते में अच्छी राशि मिलेगी। यह फैसला संघठनों की मांग के बाद लिया गया है। सरकार को डीए एरियर की मांगों का समय लग रहा था। सभी के लिए यह खुशखबरी है। अब कर्मचारियों का इंतजार खत्म हो रहा है। आधिकारिक तारीख का ऐलान अभी नहीं हुआ है।
मीडिया की रिपोर्टों के अनुसार, भुगतान जल्द हो सकता है। कर्मचारियों और पेंशनभोगियों के लिए यह अच्छी खबर है। डीए एरियर का इंतजार था, जो अब खत्म हो रहा है। इससे सभी को संतुष्टि होगी। यह विकल्प अब उपलब्ध हो रहा है। सरकार का फैसला कर्मचारियों के लिए समर्थन है। अब हर कोई इस खुशखबरी का इंतजार कर रहा है। डीए एरियर की राशि जल्द हर किसी के खाते में जा सकती है।
इतने महीने का डीए एरियर आएगा अकाउंट में
कर्मचारियों और पेंशनधारियों की बल्ले-बल्ले की खबर है। मोदी सरकार ने 1 जनवरी 2020 से 30 जून 2021 तक डीए एरियर नहीं भेजा। यह मांग लंबे समय से चल रही है। कर्मचारियों का दिल जीतने का यह निर्णय आत्म-समर्पण का परिणाम है। वायरस संक्रमण काल ने सभी को मार लिया। सरकार का नया निर्णय सबका मनोबल बढ़ाएगा। कर्मचारियों की मेहनत का सच्चा सम्मान हुआ। यह निर्णय जनता के लिए एक बड़ी राहत है। सबका विश्वास सरकार में बढ़ रहा है। समाज को यह संकेत मिल रहा है कि सरकार मन में है। साथी कर्मचारियों को समय पर मिलेगा उनका अधिकारिक मान्यता। इस निर्णय से सरकार का समर्थन बढ़ेगा। समृद्धि की राह पर आगे बढ़ेंगे सभी कर्मचारी। साथ-साथ भारत का विकास करेंगे सभी। यह निर्णय देश के लिए एक उत्तम कदम है।
अन्य जुड़ी खबरे पढ़ें: 7th pay commission Date: दिवाली से पहले सरकारी कर्मचारियों के लिए सरकार ने खोली तिजोरी, इस दिन बढ़े हुए DA के इस खाते में आएगी सैलरी
डीए का पैसा जमा
सरकार किसी भी दिन डीए का पैसा जमा कर सकती है। उच्च स्तर के कर्मचारियों के खाते में 2 लाख 18 हजार रुपये डालने की संभावना है। यह सुझाव लगभग 1 करोड़ परिवारों को लाभ पहुंचा सकता है। सरकार का यह बड़ा ऐलान नए साल से पहले हो सकता है। यह ऐलान लोगों के दिलों को जीतने के लिए काफी सक्षम है। डीए अकाउंट में राशि जमा करने की योजना को चर्चा की जा रही है। उच्च स्तर के कर्मचारियों के लाभकारी बनने की संभावना है।
- इस नई स्कीम से अनेक लोग आर्थिक सहायता प्राप्त कर सकते हैं।
- सरकार ने नए साल के अवसर पर यह योजना शुरू करने का विचार किया है।
- इस स्कीम से समाज के अधिकांश वर्गों को लाभ हो सकता है।
- यह नया पहलु विभिन्न वर्गों को समृद्धि दिलाने का उद्देश्य रखता है।
- इस कदम से लोगों के बीच आर्थिक स्थिति में सुधार हो सकता है।
- डीए अकाउंट में राशि जमा करने की योजना को बहुत सकारात्मक दृष्टि से देखा जा रहा है।
- यह एक बड़ा कदम हो सकता है जो लोगों की आर्थिक स्थिति में सुधार ला सकता है।
- नए साल के आगामी अवसर पर सरकार का यह निर्णय अच्छे दिनों की संकेत सबित हो सकता है।
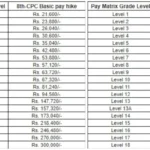
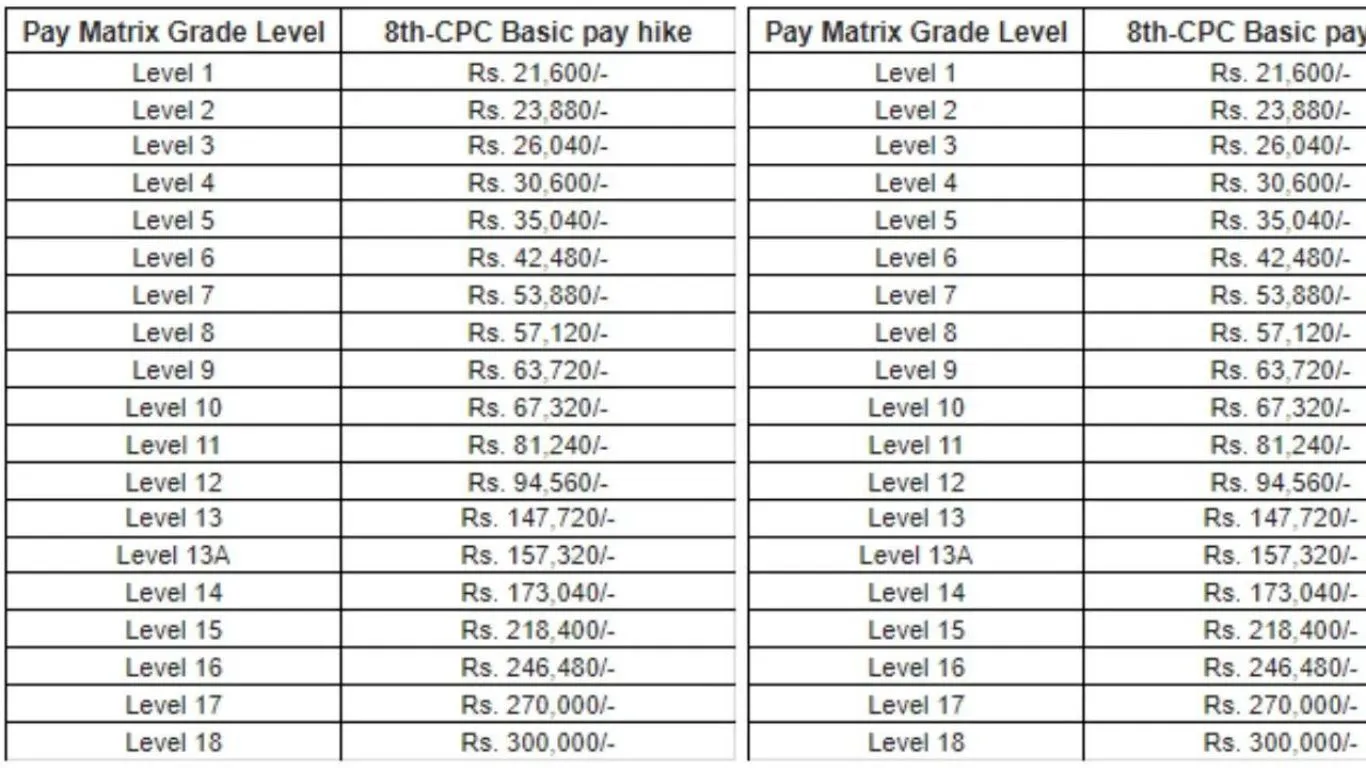
फिटमेंट फैक्टर में भी होगी बढ़ोतरी
केंद्रीय कर्मचारियों के फिटमेंट फैक्टर में इजाफा हो रहा है। इसके पश्चात्, बेसिक सैलरी में रिकॉर्डतोड़ वृद्धि होगी। सरकार फिटमेंट फैक्टर को 2.60 से 3.0 बढ़ा सकती है। यह सुनिश्चित करेगा कि अधिक संख्या में कर्मचारियों को लाभ हो। इससे लोगों का आत्म-विश्वास बढ़ेगा और सरकार को उनका समर्थन मिलेगा। सरकार चुनाव से पहले यह निर्णय ले सकती है।
- आठवें वेतन आयोग पर सरकार जल्द बड़ी सौगात दे सकती है।
- यह एक बड़े ऑफर की तरह होगा जो लोगों को प्रेरित करेगा।
- कर्मचारियों के लाभ के लिए यह कदम महत्वपूर्ण है।
- सरकार ने जनता के भले के लिए यह उत्तरदाता कदम उठाया है।
- इससे कर्मचारियों का जीवन गुणवत्ता से भर जाएगा।
- वेतन वृद्धि से सरकार का समर्थन बढ़ेगा।
- यह निर्णय सरकार की उपयोगी योजनाओं का हिस्सा है।
- कर्मचारियों को उनके योगदान का मौका मिलेगा।
- यह विकास और समृद्धि की दिशा में एक कदम है।
| Whatsapp Channel | Join |
| Telegram Channel | Click Here |
| Homepage | Click Here |